Published Dec 15, 2022 by Xiph
Application control is one of the most important mitigation strategies in ensuring the security of your business systems from malware and other cyber attacks. Application control can not only prevent the execution and spread of malicious code, but it can also prevent the modification of sensitive files without permission, and the installation or use of unapproved applications.

What is application control?
Application control is a security measure designed to protect applications on your business network against malicious code (malware), hacker intrusion and internal misconfigurations, like unapproved installation of applications or unauthorised applications processing data in a way that puts your organisation at risk of a serious breach.
Application controls typically vary depending on the business and the specific purpose of each application on your network, but the main objective is to help ensure the privacy and security of data used by and transmitted between applications. Here are the most common application control functions:
- Completeness checks controls: Ensure records processing from initiation to completion.
- Processing controls: Ensure all incoming data is valid before input into information systems.
- Identification/authorisation controls: Verify each application user’s identity and ensure access to the application system by approved business users only. Not all users need the same level of access to applications.
- Authentication controls: Provide an application system with two or more authentication methods.
- Input controls: Ensure the data accuracy and integrity feeding into the application system from upstream sources.
- Output controls: Secure all data that’s transmitted between applications and distributed.
How does application control work?
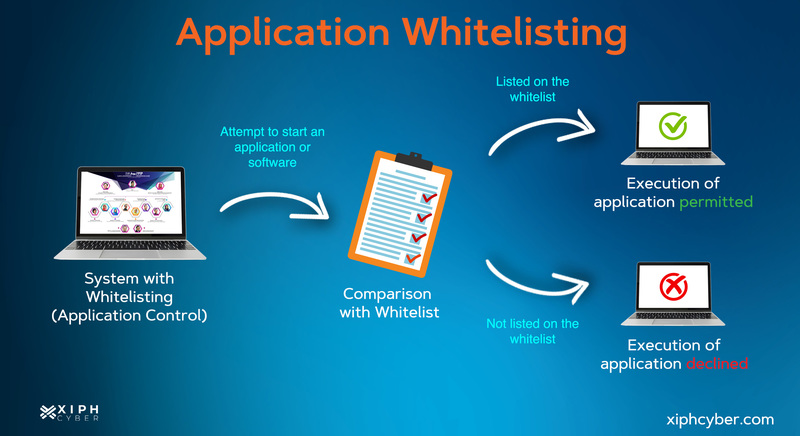
Application control monitors and manages network traffic flow to predefined rules, meaning queries need to respect certain requirements to enter your business network and to communicate with applications. When implemented properly, it ensures only approved applications (i.e. software libraries, scripts, installers, compiled HTML, HTML applications, control panel applets and drivers) can be executed.
Said requirements are what enable application control to ascertain which traffic flow comes from where in the system. Taking this into account, you can prioritise what programs you whitelist (those allowed to run) and blacklist (those you block), as well as which ones need closer monitoring.
How to implement application control
There are various ways to implement application control for your business and the most common methods used by organisations include:
- Identifying approved applications
- Adding application control rules to ensure only approved applications are allowed to execute and that only authorised users are given access to these applications
- Maintaining the application control rules using a change management program
- Validating/refining application control rules on an annual or more frequent basis.
In addition to preventing the execution of unapproved applications, application control also helps to identify attempts to execute malicious code. Drive-by downloads, or unintentional downloading of files from a website, and malicious email attachments are the most common causes of malware incidents. These cyber breaches can be prevented by simply configuring application control to generate event logs for allowed and blocked executions. These event logs should ideally contain file names, date/time stamps and the username(s) of the person(s) attempting to execute the file(s).
Just keep in mind that application control should not replace your anti-virus and other security software already in place on your systems but should be deployed as an added security layer to those.
Read more: Common types of malware & how to avoid them
Application control vs general controls
Application control is more specific to an organisation’s individual computerised applications, like payroll systems, order processing, databases, desktop publishing programs, etc. It checks that all data is valid and entered in the required format before allowing it into your system. Input controls authenticate all data entering your system, while processing controls verify the data and information being transmitted is complete and accurate, and output controls validate all information being sent out of the system.
Application control remains one of the most effective ways to mitigate the threat of executable file-based malware. It has an inherent advantage over general controls like firewalls and traditional anti-virus software in that it’s much more targeted. On the flip side, general controls apply to all areas of your business including its IT infrastructure and support services.
Why is application control important?
Application control is a crucial line of defence to safeguard data transmitted between users and applications. Every time data or information is transmitted from one user or application to another, your business is at risk of compromising its data. Information technology (IT) controls help mitigate the risks of using these tools by putting various checks in place. These checks authenticate applications and data before it’s allowed into or out of your organisation’s internal IT system, ensuring that only authorised users can manipulate the company’s digital assets.
Businesses should also conduct regular application control audits to analyse and categorise every software and application and their necessary controls. This ensures all transactions and data hold up to their specific rules and parameters.
Best application control solutions for businesses
Application control has come a long way since the days of manually configuring policies and rules, and now comes as a standard component of endpoint protection software and can be built into next-generation firewalls. While your business can save resources and time by simply using the application controls that come with an existing suite of endpoint protection security which can tell you which programs or actions should or should not be executed or use existing application control features that come with your operating systems, it’s best to implement application controls tailor-made to your business’ structure and regulatory requirements.
It’s important to ensure that application control is installed on all your business devices that enforce application control policies, including servers, laptops, and mobile devices. These policies should be automatically managed and updated using learned behaviour and other algorithms. Lastly, your organisation should enforce the principle of least privilege which limits an end user’s ability to bypass application control policies. This limits users’ permission to modify a file or write a new file to the folder to execute an untrusted file.
A final word
Automating application control can help businesses bolster the three lines of defences (input, processing, and output), to deliver the highest level of cyber security and level of assurance to all stakeholders. For more information, contact us via email: enquiries@xiphcyber.com.
Posted in: Security


